Understanding User Security in Acumatica
Posted on: December 9, 2019 | By: Brad Weinstein | Acumatica
Within many business systems, there is always a need for the collection, storage, and processing of sensitive corporate data – which must be protected against unauthorized access, use, and disclosure. Acumatica ERP is no different, and in order to protect this data, user security is broken down into four different elements: administering user accounts, restricting access to information, enforcing site security policies, encrypting sensitive data.
Administering User Accounts
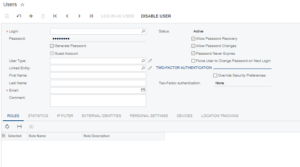
In order to have access to Acumatica an individual must have an account, which consists of a login, password, email address, among other information. These accounts can be either created locally so that they are only available in Acumatica or can be integrated with other identity management systems such as Microsoft Active Directory and Microsoft Azure Active Directory so that users can login using their domain accounts. It is important to note that the domain accounts can only be used if Acumatica is installed on your organization’s intranet.
Restricting Access to Information
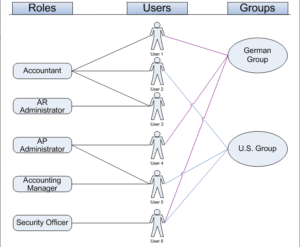
In Acumatica, user access is administered using roles specifying duties. Users belong to customized, task based roles. The access of these roles can be managed on an individual level, as each role can be granted access to a unique combination of suites, modules, forms, and form elements. In addition to limiting access, Acumatica allows you to create something called Restriction Groups, which controls the visibility of records or entities. For example, Restriction Groups can be used to limit a user’s visibility to certain General Ledger accounts, sub-accounts, vendors, or customers.
Enforcing Site Security Policies
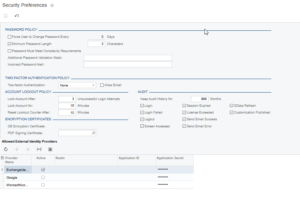
Acumatica provides various tools for to implement organizational security regulations. Some of these regulations include system wide policies for user accounts, password criteria, and security auditing. One example of a system wide account policy would be to set a standard for how many failed login attempts a user try before being locked out of the system. This configuration can help to stop any unauthorized personal from gaining system access through guessing a password.
Encrypting Sensitive Data
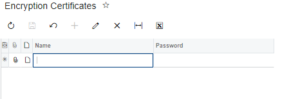
Acumatica uses digital certificates to store sensitive information in the encrypted database and to authenticate documents that are shared. These certificates each have a unique password that can be used to validate the owner if you need to reinstall the system or move the database. One useful feature of Acumatica’s encryption is that you can use an encryption certificate to sign a PDF file which is generated, and the PDF certificate protects the authenticity of the document.
Logan Consulting is a professional services firm committed to helping businesses improve business processes to get the most from their ERP investments.
Does it make sense to talk with us? Contact us to start a dialog
